Install Kubernetes Agent
The CloudZero Agent for Kubernetes collects and forwards container metrics to CloudZero, combining them with data from your cloud provider to determine how to allocate your Kubernetes costs.
You can find the Latest version in GitHub.
Supported Kubernetes installations
The CloudZero Agent supports the following Kubernetes installations:
- Self-managed Kubernetes in AWS, Azure, and Google Cloud
- AWS Elastic Kubernetes Service (EKS)
- Azure Kubernetes Service (AKS)
- Google Kubernetes Engine (GKE)
Set up the CloudZero Agent
CloudZero recommends installing the CloudZero Agent for Kubernetes in the
cloudzeronamespace. Do not install the agent in the default namespace.
Prerequisites for the CloudZero Agent
- Helm v3+
- Kubernetes v1.23+
- CRI-compliant runtime (e.g., containerd)
- A CloudZero API key with the following scopes:
container-metrics_v1:abandoncontainer-metrics_v1:get-statuscontainer-metrics_v1:legacycontainer-metrics_v1:uploadinsights:read_insights
- Each Kubernetes cluster must have a route to the internet and a rule that allows egress from the agent to the CloudZero collector endpoint at https://api.cloudzero.com on port 443
Helm installation (recommended)
helm upgrade --install cloudzero \
--repo https://cloudzero.github.io/cloudzero-charts cloudzero-agent \
--namespace cloudzero --create-namespace \
--set apiKey=<CLOUDZERO_API_KEY>
--set clusterName=<NAME_OF_YOUR_CLUSTER>Raw YAML installation
You can run helm template against the CloudZero chart to generate flat manifests that can be deployed directly.
helm template cloudzero \
--repo https://cloudzero.github.io/cloudzero-charts cloudzero/cloudzero-agent \
--namespace cloudzero --create-namespace \
--set apiKey=<CLOUDZERO_API_KEY>
--set clusterName=<NAME_OF_YOUR_CLUSTER>
kubectl apply -f cloudzero.yamlValidating the install
If all went well, you should have received an install success message letting you know that the agent has been installed.
View CloudZero Agent for Kubernetes Cost Data
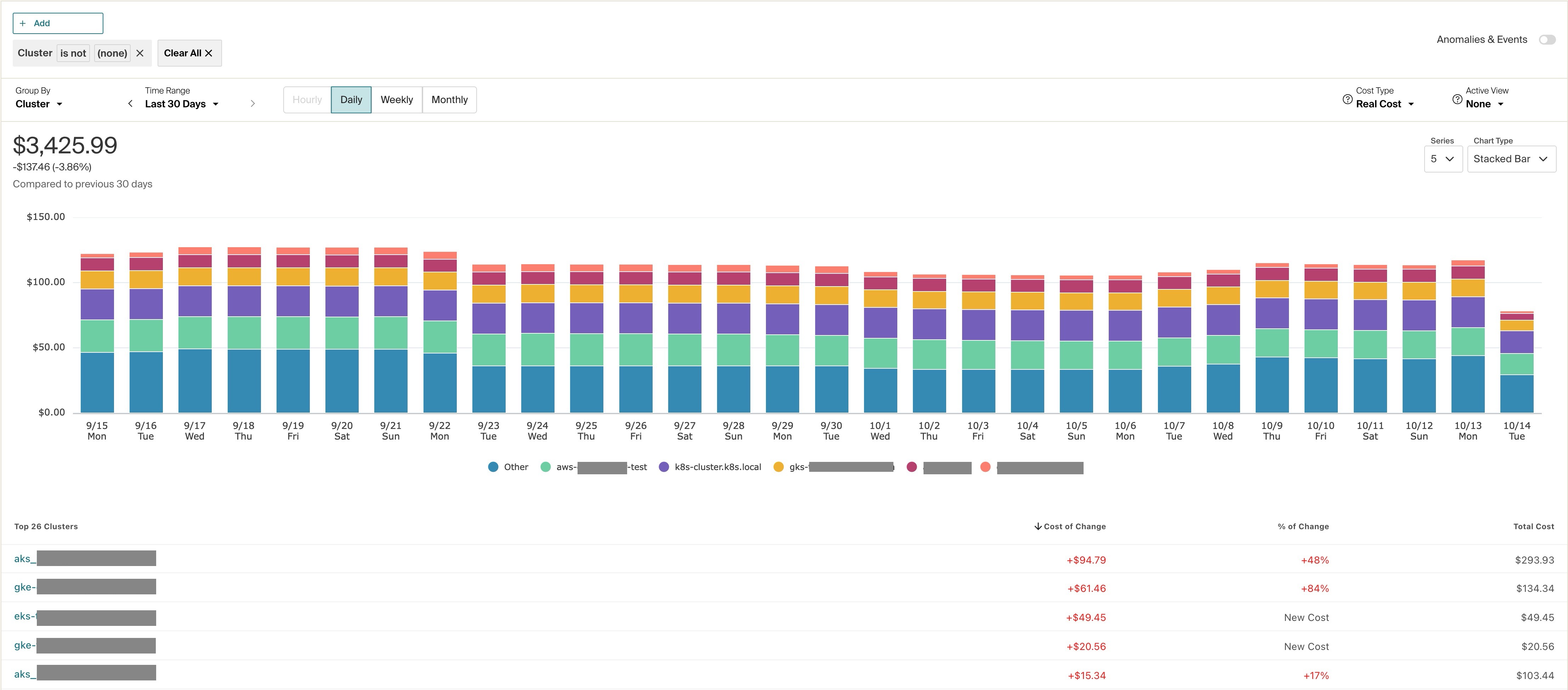
After your CloudZero agent is installed, wait at least 48 hours for data collection to occur. Then you can view it in CloudZero. For example, the following image shows Kubernetes cost data grouped by cluster:
Updated 23 days ago
